DevSecOps & Cybersecurity: Shifting Security Left with Zero Trust Architectures
DevSecOps & Cybersecurity: Shifting Security Left with Zero Trust Architectures
Introduction
In today’s digital era, traditional approaches to cybersecurity are no longer sufficient. As organizations adopt Agile and DevOps practices, security must be integrated early in the development lifecycle. This approach, known as DevSecOps, ensures that security is not an afterthought but a continuous, automated process.
At Prabha Technologies, we advocate shifting security left and embracing Zero Trust architectures, creating resilient systems that protect enterprises against evolving threats.
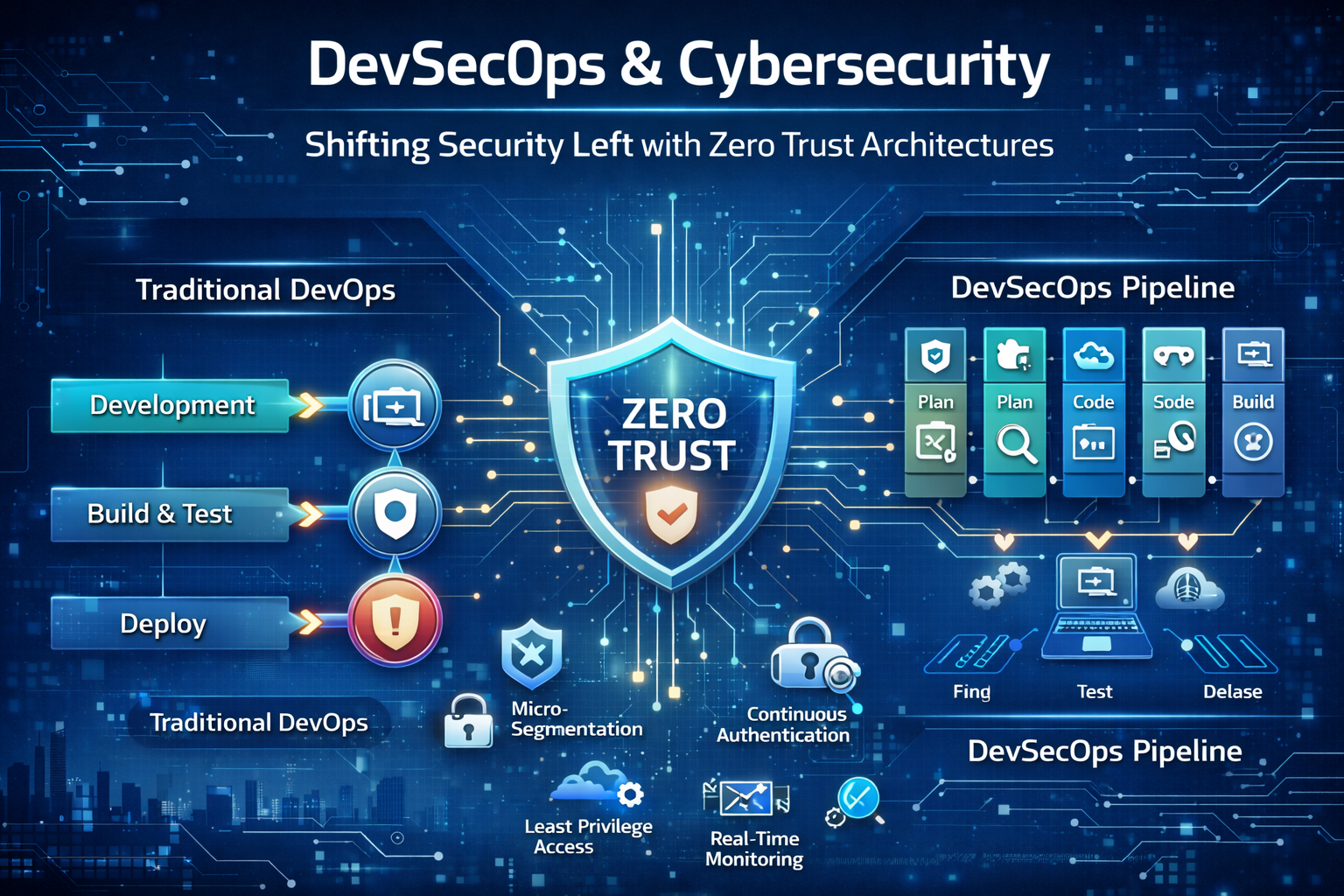
What Is DevSecOps?
DevSecOps is the practice of embedding security practices into the DevOps lifecycle, enabling teams to:
-
Detect vulnerabilities early
-
Automate security checks and compliance
-
Integrate security in CI/CD pipelines
-
Foster a culture where security is everyone’s responsibility
Instead of treating security as a final stage, DevSecOps aligns development, operations, and security teams, reducing risk while accelerating delivery.
Shifting Security Left
Shifting security left means addressing security concerns during the earliest stages of software development, including:
-
Planning & design: Threat modeling and secure design principles
-
Code development: Static Application Security Testing (SAST) and secure coding practices
-
Testing & integration: Dynamic Application Security Testing (DAST), dependency scanning, and automated vulnerability checks
-
Deployment & monitoring: Continuous security monitoring, runtime protection, and audit logs
The benefits of shifting left include faster remediation, lower cost of fixing vulnerabilities, and stronger overall security posture.
The Role of Zero Trust Architecture
Zero Trust is a security framework where no entity is trusted by default, whether inside or outside the network. Key principles include:
-
Verify every request: Continuous authentication and authorization
-
Least privilege access: Grant minimal permissions required for tasks
-
Micro-segmentation: Isolate network resources to prevent lateral movement
-
Continuous monitoring & analytics: Detect anomalies and respond in real-time
-
Device and identity validation: Ensure endpoint compliance and identity assurance
Combining DevSecOps with Zero Trust ensures secure software delivery pipelines while protecting enterprise data and infrastructure.
DevSecOps & Zero Trust in Action
1. CI/CD Pipeline Security
-
Integrate automated security scans in build and deployment pipelines
-
Block deployments with critical vulnerabilities
-
Enable real-time alerts and dashboards for security insights
2. Cloud Security
-
Enforce access control policies across cloud services
-
Monitor configuration compliance
-
Implement continuous cloud workload protection
3. Application & API Security
-
API gateway protection and threat detection
-
Code signing and secure artifact repositories
-
Automated penetration testing and fuzzing
4. Governance & Compliance
-
Automated compliance checks for ISO 27001, SOC 2, GDPR, HIPAA
-
Security as code for auditability
-
Real-time reporting for regulators and internal governance
Why DevSecOps & Zero Trust Matter
-
Proactive security instead of reactive fixes
-
Reduced attack surface and breach impact
-
Faster software delivery with integrated security
-
Enhanced trust with stakeholders and customers
-
Compliance readiness and audit transparency
Enterprises adopting DevSecOps with Zero Trust principles are better prepared to counter modern cyber threats while accelerating innovation.
Prabha Technologies’ Approach
At Prabha Technologies, we design secure-by-design software solutions by:
-
Integrating DevSecOps pipelines for CI/CD automation
-
Implementing Zero Trust architectures across cloud and on-premise infrastructure
-
Conducting continuous threat modeling, monitoring, and remediation
-
Providing enterprise-ready compliance reporting
Our goal is to deliver software that is secure, scalable, and resilient in an ever-changing threat landscape.
References
-
NIST – Zero Trust Architecture Special Publication 800-207
-
Gartner – DevSecOps: Embedding Security in DevOps
-
OWASP – DevSecOps Guidelines & Best Practices
-
Forrester – The State of Zero Trust Security
-
Microsoft – Integrating Security in CI/CD Pipelines
-
CSA (Cloud Security Alliance) – DevSecOps and Cloud Security Practices







































